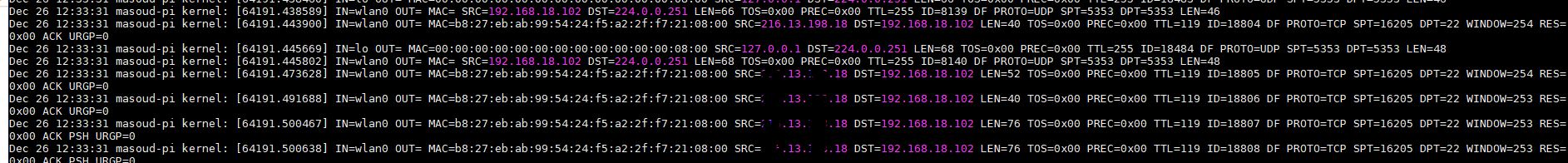
With this method you can easily identify all the traffics like source IP address (SRC) and Destination IP (DST) also you can check the Destination port (DPT)
in the above screenshot , i have a lot of packets for SSH (DPT=22) because i am remotely connected to my Raspbery Pi , if i put a deny any any rule without opening my SSH then i’ll lose my remote connection!
so that’s why this LOG line is really useful , technically we can check it , add accept rule and when we are sure that there is no other traffic that must be allowed we then add a deny any any at the bottom of the iptables chain
Well after examining messages log file it’s obvious that we need a rule for SSH, so i am going to add the following :
# sudo iptables -t filter -I INPUT 1 -p tcp -s <SRC address from log file> –dport 22 -j ACCEPT
so basically i am working on filter table (-t filter ) which is the default table and even we can omit it from our command and then i am using (-I ) for insert the rule !
if you compare this command with the previous one, i was suing (-A) for appending the rule! since the order of the rules are important and iptables are going to check all the matches from the top to bottom
then i am going to insert the rest of rules at the top of the chain !
with (-p ) i am mentioning the protocol and (-s ) is the source IP address which you should decide from where you wanna access your Pi and then with (–dport ) i am mentioning destination port 22 for SSH
it’s up to you to add more accept rules for the legit traffic other than that there are couple of rules that i usually suggest to add in order to make sure everything is working smoothely :
# sudo iptables -t filter -I INPUT 1 -i lo -j ACCEPT >>> This is for allow loopback
# sudo iptables -t filter -I INPUT 1 -m state –state ESTABLISHED,RELATED -j ACCEPT >>> For allow all Established and related traffic
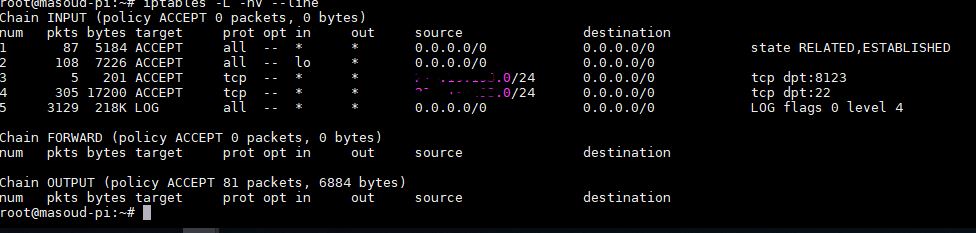
so at this stage my iptables rules are as below :
But as you can see we are not denying any traffic at the bottom of the chain we need to add a deny rule after rule 5 to block unneccassry traffic and we can easily achive this with :
# sudo iptables -t filter -A INPUT -j DROP
That’s mostly it , you can also do the same thing for other chains and remove the LOG at the end.